Mastering NPM: From Dependencies to Defense in the JavaScript Ecosystem
In the vast and ever-evolving world of modern web development, few tools are as foundational and ubiquitous as the Node Package Manager, or NPM. It is the lifeblood of the Node.js JavaScript ecosystem, serving as the world’s largest software registry. For millions of developers, `npm install` is the first command typed when starting a new project, unlocking a universe of open-source libraries, frameworks, and tools. This powerful dependency management system has revolutionized how we build software, enabling rapid development and fostering a vibrant community of collaboration. However, this immense power comes with inherent risks. The very interconnectedness that makes NPM so valuable also makes it a prime target for supply chain attacks, where malicious code can infiltrate projects through compromised dependencies. This article provides a comprehensive guide to mastering NPM, covering its core concepts, practical workflows, and, most importantly, the critical security practices needed to defend your applications in today’s threat landscape.
The Foundations of NPM: More Than Just a Package Manager
At its core, NPM is a command-line tool and an online registry. The registry is a massive public database of JavaScript packages, and the command-line interface (CLI) is the tool developers use to interact with it—installing, updating, and managing these packages. But its role extends far beyond simple installation. It’s a project management tool that ensures consistency, reproducibility, and scalability for projects of any size.
The Central Nervous System: package.json and package-lock.json
Every Node.js project that uses NPM is defined by a `package.json` file. This JSON file acts as the project’s manifest, containing crucial metadata. It lists the project’s name, version, description, and, most importantly, its dependencies.
dependencies: These are the packages required for the application to run in production (e.g., React, Express.js, Lodash).devDependencies: These packages are only needed for development and testing (e.g., Jest, Webpack, ESLint). They are not included in the final production build.scripts: This section defines command-line scripts to automate repetitive tasks like starting a development server, running tests, or bundling the application for production.
Here is a practical example of a `package.json` file for a simple React Tutorial project:
{
"name": "modern-js-app",
"version": "1.0.0",
"description": "A modern JavaScript application.",
"main": "index.js",
"scripts": {
"start": "react-scripts start",
"build": "react-scripts build",
"test": "jest",
"eject": "react-scripts eject"
},
"dependencies": {
"react": "^18.2.0",
"react-dom": "^18.2.0",
"axios": "^1.6.2"
},
"devDependencies": {
"@testing-library/jest-dom": "^5.17.0",
"@testing-library/react": "^13.4.0",
"jest": "^29.7.0",
"webpack": "^5.89.0"
},
"author": "Your Name",
"license": "ISC"
}While `package.json` defines the dependencies you want, the `package-lock.json` file records the exact version of every package that was installed. This file is automatically generated and is critical for ensuring that every developer on a team, as well as the CI/CD pipeline, installs the identical dependency tree. This prevents the “it works on my machine” problem and guarantees deterministic, reproducible builds.
Practical NPM Workflows and Commands
Understanding the daily-use commands is essential for an efficient development workflow. From initializing a project to running complex build scripts, NPM provides a rich set of tools to manage the entire application lifecycle.
Installing and Managing Dependencies
The most common NPM command is `npm install`. When run without arguments in a project directory, it installs all dependencies listed in `package.json`.
To add a new package, you specify its name:
# Install Express.js and add it to "dependencies"
npm install express
# Install Jest as a development dependency
npm install jest --save-dev
# or using the shorthand
npm i -D jest
# Install a package globally (e.g., for CLI tools like create-react-app)
npm install -g create-react-appIt’s important to understand Semantic Versioning (SemVer), which NPM uses to manage package versions. The `^` (caret) and `~` (tilde) prefixes in `package.json` allow for automatic updates to minor and patch versions, respectively. While convenient, this can introduce unexpected changes. The `package-lock.json` file mitigates this risk by locking down specific versions.

Automating Tasks with NPM Scripts
The `scripts` section in `package.json` is a powerful feature for task automation. Instead of remembering long, complex commands, you can define simple aliases. This is standard practice in virtually all JavaScript Frameworks, including React, Vue.js, and Angular.
Consider a project using Webpack as a bundler and Jest for testing. The scripts might look like this:
{
"scripts": {
"start": "node server.js",
"dev": "webpack-dev-server --mode development",
"build": "webpack --mode production",
"test": "jest --watchAll",
"test:ci": "jest --ci --coverage"
}
}You can then execute these tasks with a simple command:
# Start the development server
npm run dev
# Run tests for a continuous integration environment
npm run test:ciThe Security Imperative: Defending Your NPM Supply Chain
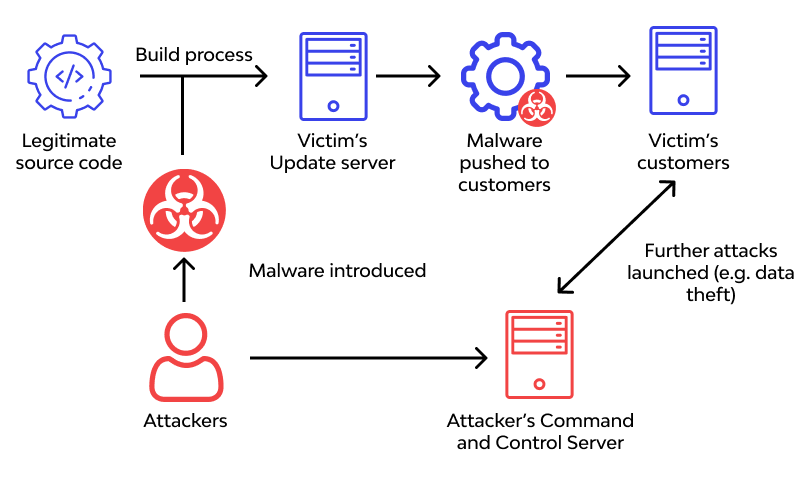
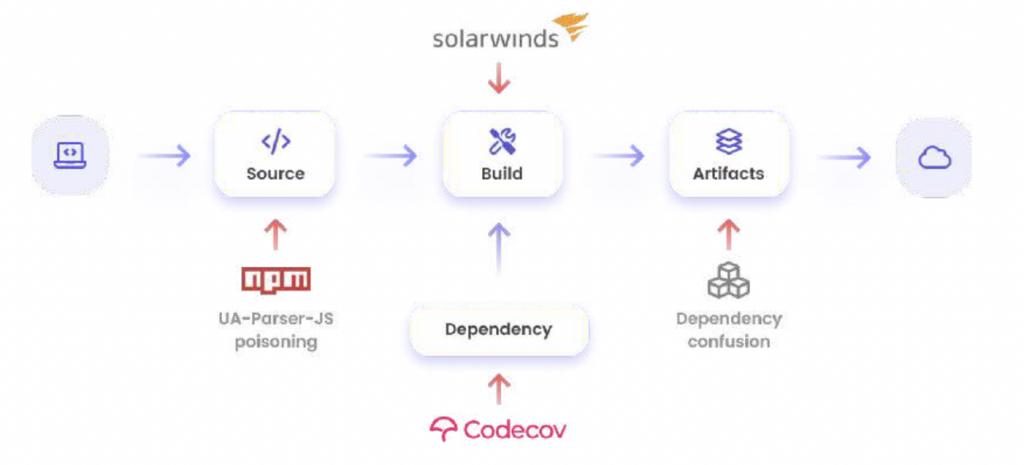
The greatest strength of NPM—its vast, open-source registry—is also its most significant vulnerability. Every package you install is code written by someone else, and each of those packages has its own dependencies, creating a complex, sprawling dependency tree. A single malicious package, whether through typosquatting (e.g., `reactt` instead of `react`), a compromised maintainer account, or a dependency confusion attack, can inject malware into your application. This makes JavaScript Security a paramount concern for every developer.
Auditing Your Dependencies with `npm audit`
NPM provides a built-in tool to help combat these threats: `npm audit`. This command cross-references all the packages in your `package-lock.json` file against the npm vulnerability database, reporting any known security issues.
Running the command is straightforward:
npm auditThe output provides a detailed report, categorizing vulnerabilities by severity (low, moderate, high, critical) and explaining the potential impact. It will often suggest a path to remediation. For many issues, a simple fix is available:
# Attempt to automatically fix vulnerabilities by updating packages
npm audit fix
# Forcing a fix can introduce breaking changes, use with caution
npm audit fix --forceHowever, `npm audit fix` cannot resolve all problems, especially those requiring a major version bump (which could introduce breaking changes) or those for which no patch is yet available. In these cases, manual intervention and research are required. Regularly running `npm audit` in your CI/CD pipeline is a crucial first line of defense.
Executing Packages Safely with `npx`
Bundled with NPM since version 5.2, `npx` is a package runner that allows you to execute commands from an NPM package without installing it globally or locally. This is incredibly useful for scaffolding tools and one-off scripts.
For example, instead of globally installing `create-react-app`, you can run it directly:
npx create-react-app my-awesome-projectThis ensures you are always using the latest version of the tool and avoids cluttering your global namespace with packages you might only use once. From a security perspective, it reduces the attack surface of globally installed packages that could become outdated and vulnerable.
Advanced Strategies and Best Practices for NPM
To truly master NPM and build robust, secure applications, you must go beyond the basic commands and adopt a set of professional best practices. These strategies focus on security, performance, and maintainability.
Embrace the Lockfile
Always commit your `package-lock.json` (or `yarn.lock` / `pnpm-lock.yaml`) file to version control. This is non-negotiable. It is the single source of truth for your project’s dependency tree, guaranteeing that every installation is identical across all environments. This is fundamental for Clean Code JavaScript practices and team collaboration.
Automate Security Scanning
While `npm audit` is a great start, professional teams should integrate automated security scanning into their workflows. Tools like GitHub’s Dependabot, Snyk, or Sonatype continuously monitor your repositories, automatically creating pull requests to update vulnerable dependencies as soon as patches are released. This proactive approach is a cornerstone of modern JavaScript Best Practices.
Consider NPM Alternatives: Yarn and pnpm
NPM is the default, but it’s not the only option. Yarn and pnpm are popular alternatives that offer distinct advantages.
- Yarn: Developed by Facebook, it introduced features like lockfiles and improved performance that were later adopted by NPM. Its modern versions (Berry) offer innovative features like Plug’n’Play for faster installations.
- pnpm: Stands for “performant npm.” Its main advantage is efficiency. It uses a content-addressable store to save disk space and dramatically speed up installations by linking files from a global store instead of copying them. This approach also offers a stricter, less-permissive `node_modules` structure, which can prevent certain classes of dependency-related bugs.
Use a `.npmrc` File for Configuration
For advanced configuration, such as connecting to a private registry (like GitHub Packages or Artifactory) or setting project-wide settings, use a `.npmrc` file. This file, placed at the root of your project, ensures that all team members use the same configuration without having to set it up manually.
Conclusion: Wielding NPM with Power and Responsibility
NPM is an indispensable tool that has fundamentally shaped modern Full Stack JavaScript development. It accelerates development, promotes code reuse, and provides access to an unparalleled ecosystem of open-source innovation. However, this power must be wielded with a deep sense of responsibility. The open nature of the registry makes it a fertile ground for security threats that can have devastating consequences.
As a developer, your journey with NPM involves more than just learning commands. It requires cultivating a security-first mindset. Make `npm audit` a regular part of your routine. Commit your lockfile religiously. Automate vulnerability scanning in your CI/CD pipelines. Stay informed about emerging threats in the ecosystem. By embracing these best practices, you can confidently leverage the immense power of NPM to build amazing, performant, and, most importantly, secure applications.